Moxa NPort W2150A: OS Command Injection Vulnerability

On this ICS/OT communication server, attackers might execute arbitrary commands, potentially leading to a complete compromise of the system.
The device bridges ethernet networks and serial devices in Industrial Control Systems, facilitating seamless data translation. It integrates legacy equipment with modern systems, preserving investments and enabling efficient communication.
Understanding the Hardware
The Moxa NPort W2150A is an Ethernet to Serial Server designed for industrial applications. It serves as a bridge between Ethernet and serial communication, allowing legacy serial devices to connect to modern Ethernet networks. With operational lifespans stretching over 20 to 30 years, ICS often operate on outdated firmware and software, rendering them susceptible to cybersecurity exploits. Moreover, the evolving threat landscape exacerbates the risk, as these systems were designed without the robust cybersecurity as in modern IT systems.
Pentest Conditions
We’ll be operating under specific conditions:
- Direct OT network access.
- Emulation of SL-2 (IEC 62443) attacker capabilities.
- Black-box/White-box approach
Let’s delve into a real-world scenario where we exploit an OS Command Injection vulnerability to establish a backdoor on a Moxa NPort W2150A communication server.
Getting Access

We begin by conducting reconnaissance on the target network to gather information about the devices and services running on it. Using tools like Nmap, we scan for open ports and identify an active web server running on port 80 of the Moxa NPort W2150A device.

Taking advantage of hardcoded credentials present in the device’s firmware, we gain access to the web interface. These credentials have been discovered through accessing the underlying Linux OS via an unprotected seriel shell over UART. With these credentials, we log in to the web interface, gaining access to administrative functions.
Exploiting Unsanitized Input Fields
Once inside the web interface, we navigate to the Maintenance section under system management. Here, we find various diagnostic and testing functions, including the ping test function.
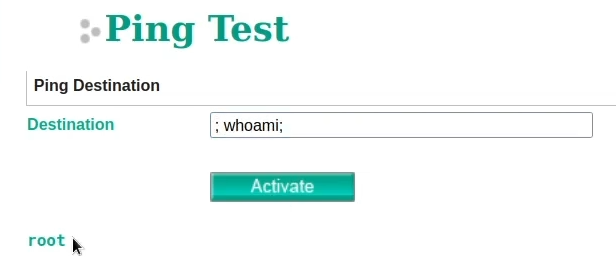
We exploit the ping test function to inject malicious commands into the input field. Typically, this input field is designed to accept IP addresses for ping tests. However, due to insufficient input validation, we can inject arbitrary commands by appending them with a semicolon (;).
The system parses the input as a single command, expecting it to be a ping command in this case. But when the system encounters the semicolon (;), it interprets it as a delimiter that separates commands. The system executes the first command before the semicolon, which might be a legitimate command like “ping”. It carries out the operation associated with that command. In this case, if no IP address is parsed, it skips this step entirely and executes the subsequent command. In this example, “whoami” is the subsequent command.
After executing the injected command successfully, we verify our elevated privileges using the “whoami” command. This command reveals that we have gained root-level access to the underlying operating system, granting us unrestricted control over the device.
Manipulating Firewall Rules and Establishing a Backdoor
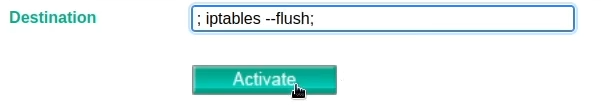
With root access, we manipulate the firewall rules using the “iptables” command. By issuing commands to delete all existing rules (double dash flush), we effectively disable any network filtering mechanisms in place, opening the system to further exploitation.
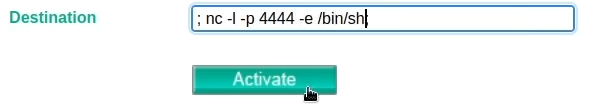
To maintain persistent access to the compromised device, we establish a backdoor using netcat (nc). We start a bind shell on a chosen port (e.g., port 4444) using the “-e” option, which allows us to execute commands through the shell.

With the backdoor established, we can remotely access the compromised device’s shell from a separate terminal using netcat. This gives us full control over the device, allowing us to execute commands, pivot within the network, and potentially compromise additional systems.
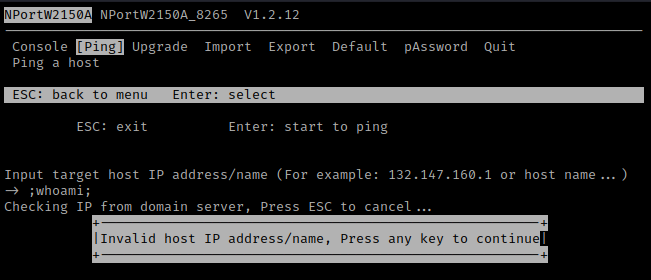
Unexpectedly, this OS injection exploit fails over the Telnet device maintenace interface. The system interprets the injected command as an invalid IP address, preventing its execution.
Mitigation Strategies
Firmware Upgrade: In response to the discovered vulnerabilities, it is imperative to upgrade the device’s firmware to the latest version available. Patching known vulnerabilities and implementing security enhancements can mitigate the risk of exploitation by malicious actors.
Network Segmentation: Implementing network segmentation can limit the impact of a compromised device by isolating critical systems from potentially compromised segments. By restricting lateral movement within the network, organizations can contain and mitigate the effects of a breach.
Regular Security Assessments: Conducting regular security audits and vulnerability assessments can help identify and address potential weaknesses in industrial communication systems. Proactive measures, such as penetration testing and code reviews, can uncover vulnerabilities before they are exploited by malicious actors.
Categories: : Pentesting
 Marcel Rick-Cen
Marcel Rick-Cen